
Wireguard vs OpenVPN vs Shadowsocks: Which One Is Better?
- December 21, 2023
- 8 minutes Read
- Network
WireGuard is more secure and provides the fastest speed, whereas OpenVPN is a direct VPN server, which offers more privacy, and Shadowsocks is more flexible and easily customizable.
While all three of these protocols- WireGuard, OpenVPN, and Shadowsocks are used in popular VPN services, the core differences act as a deciding factor for the user. This article will delve deep into the differences between the protocols and a detailed breakdown of how they work.
Comparing WireGuard, OpenVPN, and Shadowsocks
To make an informed decision about which VPN protocol to choose, consider the following factors:
1. Speed and Performance:
- WireGuard is known for its exceptional speed and efficiency.
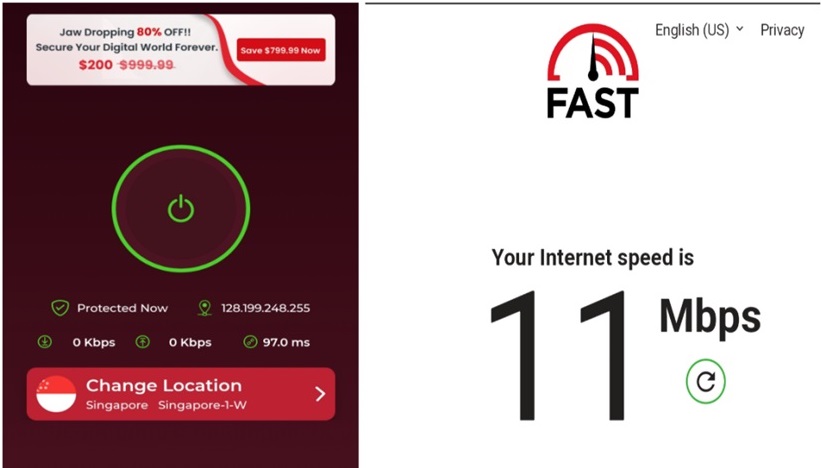
Fig 1.0 Symlex VPN connected to a Wireguard server(left) and respective Internet Speed(right)
- OpenVPN is slower in establishing connections but offers reliable performance once connected.
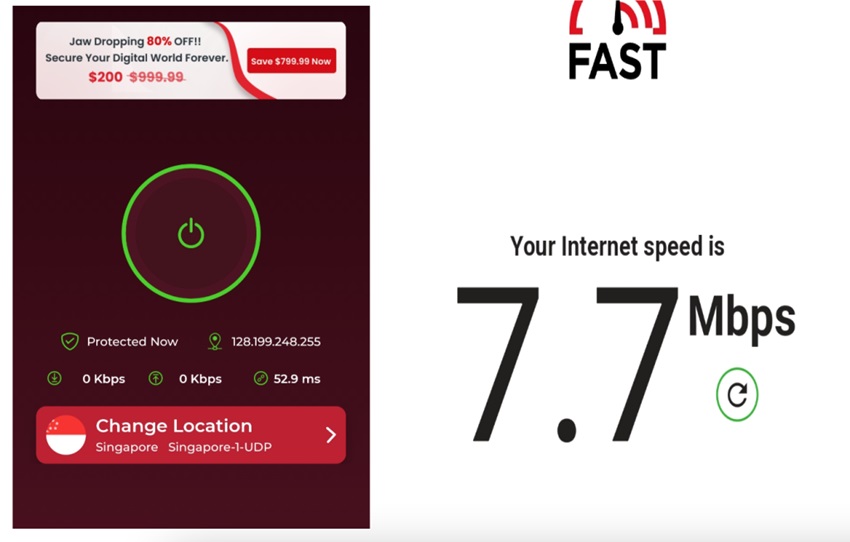
Fig 1.1Symlex VPN connected to an OpenVPN server(left) and respective Internet Speed(right)
- Shadowsocks offers decent performance, especially for bypassing censorship.
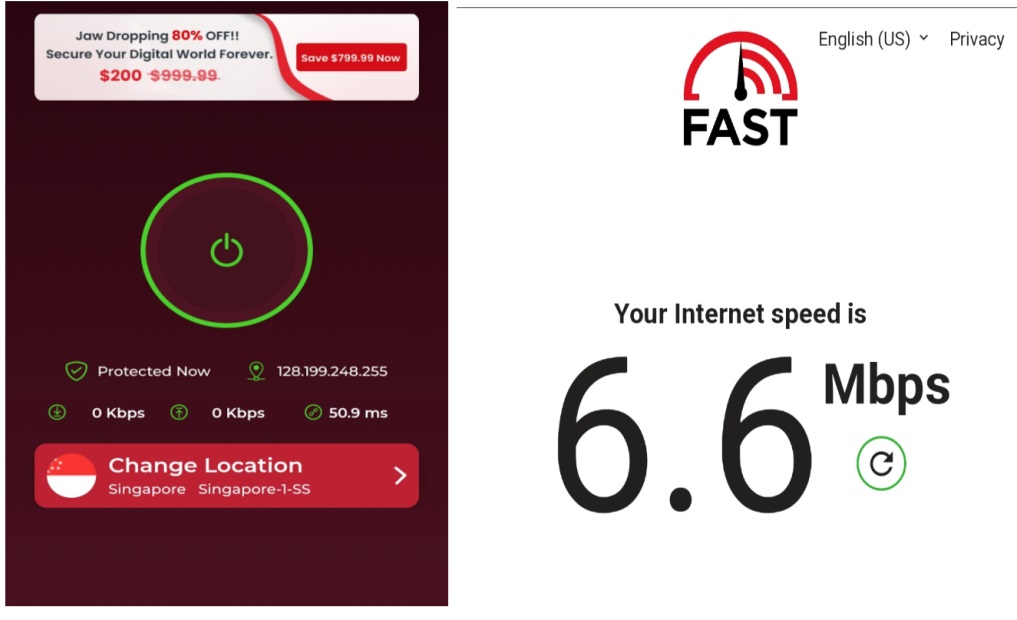
Fig 1.2 Symlex VPN connected to a Shadowsocks server(left) and respective Internet Speed(right)
2. Security:
- WireGuard employs modern cryptography and perfect forward secrecy. It uses the Cha-Cha20 encryption key.
- OpenVPN offers robust security with the use of OpenSSL or LibreSSL.
- Shadowsocks provides encryption with the AEAD Cipher key but may not be as secure as WireGuard or OpenVPN.
3. Easy To Use:
- WireGuard is user-friendly and easy to configure. It uses around 4000 lines of code.
- OpenVPN can be complex to set up, especially for beginners, as it uses around 70,000 lines of code.
- Shadowsocks is relatively simple to configure, with 6455 making it accessible to users with varying technical expertise.
4. User Experience:
- WireGuard is suitable for users seeking high-speed and secure connections.
- OpenVPN is ideal for those who require extensive configuration options and have more technical experience.
- Shadowsocks is primarily used to bypass censorship and access restricted content.
5. Resource Usage:
- WireGuard consumes minimal system resources, making it suitable for low-power devices.
- OpenVPN and Shadowsocks may require more resources, potentially impacting the performance of low-end devices.
6. Anonymity and Privacy:
- WireGuard and OpenVPN offer high levels of anonymity and privacy.
- Shadowsocks can enhance anonymity but may not provide the same level of privacy as WireGuard or OpenVPN.
7. Bypassing Restrictions:
- WireGuard and OpenVPN can bypass censorship to some extent but are not explicitly designed for this purpose.
- Shadowsocks excels at bypassing government censorship and geo-restrictions.
- ( DU and Etisalat bypassed through SS and openvpn, tested by user tester)
8. Support and Adoption:
- WireGuard is gaining popularity but may have limited third-party applications and support.
- OpenVPN enjoys wide adoption and a strong community.
- Shadowsocks is popular in regions with strict internet censorship.
What is WireGuard and How Does it Work?
WireGuard is a modern and innovative VPN protocol designed to establish secure connections between devices over the internet. It’s known to be used for its simplicity, efficiency, and robust security measures. Developed by Jason A. Donenfeld, WireGuard is gaining traction as a reliable alternative to traditional VPN protocols due to its unique encryption and network connectivity approach.
How WireGuard Works
WireGuard operates using state-of-the-art cryptographic protocols and a simpler codebase, focusing on performance and security. It aims to provide a seamless and secure VPN experience, emphasizing speed, simplicity, and the best security measures. Its innovative approach to encryption, key exchange, and network operation sets it apart from traditional VPN protocols, making it a promising choice for those seeking a balance between performance and security.
Here’s an overview of its operation:
1. Lightweight Design: WireGuard is built with a minimal codebase, with about 4000 lines of code, making it easier to audit for vulnerabilities and ensure its operation efficiency. It is easy to configure and deploy as SSH.
2. Cryptographic Foundations: It uses modern cryptography, primarily relying on the Noise Protocol Framework, alongside Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24 and HKDF. which brings together cutting-edge cryptographic simplicities to ensure robust encryption, integrity, and secure communication.
3. Key Exchange: WireGuard performs a key exchange through a process that involves public keys. It establishes secure connections over a VPN service, using these keys, ensuring that both endpoints communicate securely.
4. Dynamic Tunnels: WireGuard creates virtual network interfaces acting as secure tunnels between devices. These interfaces handle the encryption and decryption of data packets passing through them.
5. Secure Data Transfer: Once the secure tunnel is established, WireGuard encrypts all data passing through it using encryption algorithms. This encryption ensures that even if the data is intercepted, it remains unreadable without the correct decryption keys.
6. Minimal Overhead: Unlike some traditional VPN protocols, WireGuard aims to minimize the overhead in setting up and maintaining secure connections, resulting in faster connection establishment and better performance.
7. Perfect Forward Secrecy: WireGuard employs perfect forward secrecy, ensuring that even if an attacker manages to compromise a key, they cannot decrypt past traffic, enhancing overall security.
8. Cross-Platform Compatibility: It is designed to work on various platforms, from desktop operating systems like Windows, macOS, and Linux to mobile platforms such as Android and iOS.
9. Stealth Mode: WireGuard can be configured to operate on different ports, making detecting or blocking traffic more challenging for network administrators.
What is OpenVPN and How Does It Work?
OpenVPN is an open-source, versatile, and widely used VPN protocol known for its strong security and flexibility. It has existed for over two decades and is recognized for its reliability, cross-platform compatibility, and extensive configuration.
How OpenVPN Works:
OpenVPN creates a secure and encrypted connection, allowing users to access the internet through a secure tunnel. Here’s an overview of its operation:
1. Open-Source Nature: As an open-source project, OpenVPN’s source code is publicly available, allowing for community review and contributing to its seamless service and security.
2. Tunneling Protocol: OpenVPN uses a custom security protocol based on SSL/TLS (Secure Sockets Layer/Transport Layer Security). This protocol ensures secure data transmission over the internet by creating a secure and encrypted tunnel.
3. Cross-Platform Compatibility: OpenVPN is compatible with various operating systems, including Windows, macOS, Linux, iOS, and Android, providing flexibility and accessibility across devices.
4. Security and Encryption: It employs OpenSSL or LibreSSL for encryption, offering robust security measures to protect data transmitted over the network.
5. Connection Establishment: OpenVPN uses public and private keys to establish secure connections. It typically operates through two protocols: TCP (Transmission Control Protocol) for reliability and UDP (User Datagram Protocol) for speed, allowing users to choose between them.
6. Configuration Flexibility: OpenVPN is highly configurable, allowing users to set up the VPN according to their needs. It supports various authentication methods, encryption ciphers, and network configurations.
7. VPN Server and Client Configuration: OpenVPN employs a server-client architecture. Users set up a VPN server to which clients connect, creating a secure tunnel through which data is encrypted and transmitted.
8. Community Support: OpenVPN benefits from an active and engaged user community. The community provides extensive documentation, forums, and support to assist users in setting up and troubleshooting their VPN configurations.
9. Secure Remote Access: OpenVPN is often used for secure remote access to corporate networks, providing employees a secure way to access company resources from remote locations.
What is Shadowsocks and How Does It Work?
Shadowsocks is a proxy tool that enables users to bypass internet censorship and access restricted content. Initially developed in China, it has gained popularity for its ability to circumvent government restrictions and provide a secure and private connection over the Internet. Shadowsocks primarily aims to bypass government censorship and access restricted content, especially in regions with strict internet regulations. Its proxy-based approach, encryption methods, and stealth mode effectively circumvent online censorship and restrictions.
How Shadowsocks Works:
Shadowsocks operates differently from traditional VPNs as it’s a proxy-based system focusing on circumventing censorship. Here’s an overview of its operation:
1. Proxy-Based Design: Shadowsocks works as a proxy server that operates on the principle of passing encrypted internet traffic between the user’s device and the server, effectively bypassing restrictions and filters set up by internet service providers or governments.
2. Lightweight and Minimalistic: It’s designed to be lightweight and operates with minimal resources, making it suitable for low-end devices or those with limited bandwidth.
3. Encryption and Secure Tunneling: Shadowsocks uses encryption methods, such as the AEAD Cipher, “Authenticated Encryption with Associated Data,” to secure internet traffic from the proxy server. It establishes an encrypted tunnel between the user’s device and the remote server, ensuring privacy and security. Users can select from various encryption methods, offering flexibility and adaptability to suit different security needs.
4. Configuration and Server Setup: Users set up a Shadowsocks server, and client applications are configured to connect to this server, allowing encrypted internet traffic to pass through it.
5. Anonymity and Privacy: Shadowsocks provides anonymity and privacy for users by concealing their internet activity from ISPs and potential surveillance.
7. Stealth Mode: Shadowsocks can operate on different ports, making it challenging for network administrators or censors to detect and block its traffic, enhancing its effectiveness in bypassing restrictions.
8. Community Support: As an open-source project, Shadowsocks benefits from a dedicated user community that provides documentation, support, and discussions to aid users in setting up and using the proxy effectively.
Conclusion
Even though these protocols have their differences, making them slightly different from the others, they work best as one team. VPNs containing these 3 protocols will serve its users the best performance.





