
Does A VPN Protect You on The Dark Web?
- January 25, 2024
- 10 minutes Read
- Security & Privacy
Yes, a VPN can protect you on the Dark Web by hiding your original IP address from hackers and prying eyes.
VPNs with military-grade encryption, double vpn/multi-hop support, and a no-logs policy are ideal for browsing the Dark Web.
However, refrain from browsing the Dark Web with free VPNs, as they’re not safe.
The best and safest way to access the Dark Web is through “The Onion Router” or the Tor browser. A VPN helps you access the Dark Web without a third party prying and stealing your data.
What is the Dark Web?
The Dark Web is a part of the Internet that is purposefully concealed and unavailable compared to regular web browsers. It is a component of the deep web, which is the entirety of the internet that search engines have not yet indexed.
The Dark Web is purposefully hidden and can only be accessed with specialized hardware and software, like Tor. We’ll explain in detail what Tor actually is and how it is used to access the Dark Web.
3 Major Dangers of The Dark Web
Even though it might seem like a fun time browsing the Dark Web, some major dangers linger there. As a user, you must be aware of those.
Here are 3 major dangers of the Dark Web:
- Cybercrime– This is a highly punishable crime however, it is still very much in practice due to the access to media. Since the Dark Web has limited users, the risks of cybercrime are higher. Most cybercriminals do identity theft, credit and debit card thefts, as well as bullying and posting malicious comments using the Dark Web.
Do you know that phishing is the most commonly used and widely known name for this type of cybercrime?
- Unlawful activities– People who are associated with heinous and illegal crimes such as human trafficking, selling weapons, or selling drugs use the Dark Web to conduct these activities. These are not only illegal but extremely harmful to the youth who might come across any of them by accident.
- Virus and Malware: Your device might face an unwanted malware attack or virus insertion from a random click on a pop-up ad. You will be typing away on your browser meanwhile, a click on a strange ad might steal all your data. Beware!This might scare you. However, it is not entirely unsolvable due to the invention of the VPNs. Not many VPNs protect you or provide you with enough information to protect and monitor yourself on the Dark Web.
In this next segment, we’ll see how Symlex VPN provides you with the adequate protection and monitoring you need on the Dark Web.
How Does Symlex VPN Protect You from the Dark Web?
A VPN is designed to be multipurpose. However, to Dark Web users, it’s a virtual shield to protect them from all the negative aspects of the Internet.
Listed below are 7 features that make a VPN the perfect choice for a user who uses the Dark Web.
- Dark Web Monitoring: Symlex VPN has a special feature: Dark Web monitoring. As a Symlex VPN user, you will have access to the integrated Dark Web Monitoring feature in the system.
Go to “Settings” from the menu bar on your screen’s top left.
Scroll down a little to find the “Dark Web Monitoring” feature and click.
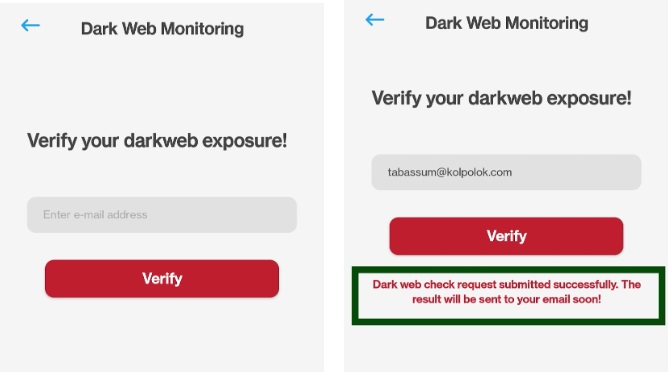
Put your Email address and click on “Verify.” Symlex VPN will verify whether your email address has ever been exposed to the Dark Web.
Please wait for the Email to arrive.

If Symlex VPN finds any Dark Web leak involving your Email ID, you will get an email like this. We prefer for you to change your password immediately in that case.
This Dark Web Monitoring system on Symlex VPN ensures and warns you on time so that none of your information is leaked online. This feature benefits users greatly in keeping themselves harmless in the vast Internet world.
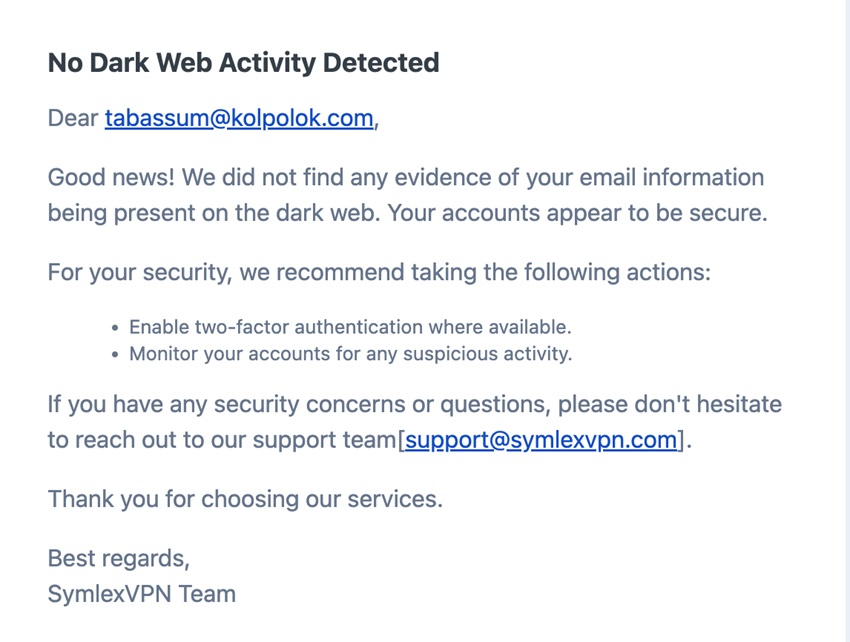
If you do not have any issues or leaks on the Dark Web, you will receive an Email like this:
2. Encryption: VPNs are well known for the type of encryption they provide. The best VPNs have the AES-256 military-grade encryption system, ensuring complete data and information privacy. When you connect your VPN before accessing the Dark Web, the encryption system creates a secret tunnel so that no data is accessible to outsiders.
3. IP Address Anonymity- VPNs have dedicated IP addresses that are assigned to create a proxy IP address for you so that no one, not even your ISP, is able to track you and access your history. These dedicated IPs replace your actual IP, which results in anonymous Internet access.
4. Range of Servers- VPNs have a large range of servers located in different regions around the world. If you want to access content unavailable in your region, you can connect your device to the server of the location where your content originates on the Dark Web.
This feature also ensures less latency and good speed due to the availability of servers.
5. Kill Switch: This is handy if you want zero compromise on your internet security. The Kill Switch immediately shuts down your internet connection at the instant you get disconnected from the VPN service.
You might get disconnected from the VPN for various reasons. That little time is enough to leave your data in the open for theft and other illegal and illicit purposes.
6. Ad-blocker: Numerous ads pop up when you are trying to enjoy browsing or watching content after a long, tiring day. This can be extremely excruciating and borderline annoying.
The ad-blockers installed in the VPN come to your rescue right then. It blocks all the random pop-ups that appear on your screen, ensuring a seamless and smooth experience for you.
7. Private Browser: Symlex VPN also has a private browser installed in its system. So, if you do not want to connect to the VPN service itself, you can connect to the private browser, which is the Tor Browser.
Advantages and Drawbacks of Using the Dark Web
There might be various legally approved reasons why we might use the Dark Web, and some of them are mentioned below:
1. Anonymity: By visiting websites with encrypted addresses, users on the Dark Web frequently maintain their anonymity. Users’ location and identity can be hidden by using a VPN.
2. Specialized Domains: Websites on the Dark Web use the “.onion” domains to signify that they are only accessible via the Tor network. The regular Domain Name System (DNS) does not include these domains
3. Restricted Access: A number of websites, markets, and content that would not be reachable or visible on the surface web are known to be hosted on the Dark Web. Certain credentials or authorizations may be needed to access particular places.
4. Diverse Content: Although the Dark Web is notorious for being a center for criminal activity, such as the selling of unlawful goods and services,it also houses legal content and provides a forum for people who need secrecy for legal purposes, such as activists and journalists.
5. Compromised Free VPNs: Most free VPN services have the tendency to sell user information due to the money offered to them. It is highly discouraged to use a Free VPN when it comes to your data and information security. Free VPNs also do not have the most features to provide the right security and anonymity on the Internet. It is preferred to use a paid VPN.
What is The Onion Router (Tor)?
We mentioned that you need a special browser to access the Dark Web. Let’s get a complete overview of The Onion Router or Tor, which helps you access the Dark Web.
Anonymous internet communication is made possible via the privacy-focused network known as Tor. It was created to shield users’ freedom and privacy from prying eyes by masking users’ location and identity through a network run by volunteers.
It has been made difficult for anyone to breach and access the source or location of a user.
How Tor Protects You On the Dark Web?
Some key factors of Tor make it more convenient for users. Some of them are as follows:
1. Anonymity: Tor passes user traffic over a network of servers or nodes for the sake of anonymity, causing delays. This makes it difficult to determine the communication’s source and destination.
2. Encryption: Every piece of information sent across the Tor network is encrypted, improving user privacy and security. Comparable to the layers of an onion, layered encryption makes sure that every node in the network can only decrypt a single layer, protecting the user’s anonymity.
3. Routing of Onions: Each node in the Tor network removes a layer of encryption from data as it moves through it due to its Onion Routing system.This process exposes the details required to forward the data to the next node. This procedure continues until the data gets to where it needs to be.
4. Access with “.onion” Domains: Tor provides access to websites bearing the “.onion” domain. These websites are not viewable with regular web browsers(Chrome or Firefox) and are hosted on the Tor network. They frequently offer more anonymity and privacy.
5. Security and Privacy: People who want more anonymity online utilize Tor extensively. It enables users to access the internet without disclosing their location or identity and get around censorship.
6. Volunteer-Operated Nodes: A decentralized network of volunteer nodes underpins the Tor network. Users’ traffic is routed through a number of these nodes to conceal its origin, which helps to strengthen and withstand the network.However, Tor is insufficient to protect your anonymity, data, and information while accessing restricted content. In the next segment, we’ll see the disadvantages of Tor.
Why Tor & VPN May Not Be Sufficient?
Despite its advantages in providing anonymity and privacy, Tor has certain drawbacks.
- One notable limitation is the potential for slower connection speeds due to the multi-layered encryption and the decentralized nature of the volunteer-operated nodes.
- The complicated traffic routing through various nodes can introduce latency or lagging, impacting the overall user experience. Moreover, Tor’s reputation has been under the rocks due to its alleged association with illegal activities on the Dark Web, raising concerns about its misuse.
- Additionally, while Tor can make communications anonymous, it does not encrypt the data once it exits the Tor network, leaving it vulnerable to interception if users are not employing end-to-end encryption.
- Lastly, some websites may block access from Tor exit nodes, limiting the accessibility of certain online content for Tor users. This can be compared to DdoS attacks. Even though Tor may come with issues, the perfect solution for it is a VPN service. In the following segment, we will see how a VPN protects you on the Dark Web.
Protect Yourself
We hope you got your answer; if you were wondering- does a vpn protect you on the Dark Web? If you are an avid Dark Web user, this is your opportunity to bag the perfect VPN for you. A VPN will be the bow and arrow to your unshielded warrior, i.e., your data and information.
So, why wait? Choose the perfect VPN for the Dark Web and let it protect your personal data and information from the world.





